- Understanding High-Poverty Environments and Employee Fraud
- Key Areas of Employee Integrity Risk in Agribusiness
- Preventive Strategies for Managing Integrity in African Agribusiness
- Implementing a Comprehensive Risk Management Framework
- Case Studies in Risk Reduction
- Leadership’s Role in Risk Management
- Leveraging technology for business integrity
- The Most Common Pitfall in Managing Business Processes
- Conclusion
I have twice had to turn around African agribusinesses that were struggling due to fraud and/or loss of control over business processes. The source of the problem was not external—clients, hackers, suppliers, or otherwise—but rather the companies' own employees misappropriating company assets.
This is a global issue: PWC’s 2022 Global Economic Crime and Fraud Survey found that 46% of surveyed organizations had suffered from fraud or other economic crimes within the previous 24 months, with employee asset misappropriation being a top-three cause. For companies in industrial manufacturing or retail, it was even a top-two cause! Furthermore, I think it is safe to assume that the actual figures are worse than what companies admit to in a survey.I did some internet research to find evidence of these numbers in Africa. The euphemistically labeled “shrinkage” for retail companies in South Africa is estimated at an eye-watering 5-7%. From anecdotal evidence of business leaders I have met in several countries on the continent, I cannot recall someone who does not have a story to share about employee misappropriation. Most would mention employee integrity as one of their key concerns.
Working in high-poverty environments, I have seen the smuggling out of goods under clothes, in bags, laundry baskets, or garbage bins, under-depositing of cash, failing to use formal systems for registering a sale, overcharging clients, theft from fuel tanks, unauthorized transport of third-party goods by company trucks, accepting uncovered checks from “friends,” writing off perfectly good products as “damaged,” charging job-seekers a fee to accept candidature files, making subordinates execute work for a “side-hustle” while on company payroll, charging employees to clock for fictitious paid overtime, clocking in colleagues when in fact they’re absent, accepting bribes from suppliers for an inflated order, accepting bribes from suppliers to accept substandard quality, etc. You get the point. Fortunately, we have been spared the disappearance of whole trucks of inventory or the wholesale emptying of warehouses overnight, which I know has happened to some colleagues. More surveillance isn’t always the answer, either. After adding guards and a camera system, I was beyond words to find a guard carrying off company goods in full view of our camera system.
Understanding High-Poverty Environments and Employee Fraud
The environments we operate in are generally high-poverty, and social security is mostly provided by the (extended) family, not the state. Social pressure from family members can tempt employees to commit fraud: they’re the ones with a formal job at a reputable business, so they should provide. It’s tempting to wave the moral finger in such situations, but I honestly don’t know what I would do in their position. I have never been in their shoes: in a situation of comparable poverty and pressure from the entire extended family to provide “a solution” for grandma’s hospital bill or the treatment of a sick child. I’d like to think I’d do the right thing and find a lawful solution, but you can only ever tell once you’ve been in that position. Sometimes, theft is not always seen as a problem: “you’re only a thief if you get caught; otherwise, you’re just clever.” Regardless of whether you have sympathy for the motives of the employee, you cannot run a business where “pilferage” is part of daily practice.
If you operate in a high-poverty environment and have trouble recognizing any of the above, you definitely have a problem. As a variant of Murphy’s law states, “if everything seems to be going well, you have obviously overlooked something.” For your African agribusiness, mastering employee integrity issues is a key competitive advantage and a precondition for growth.
Key Areas of Employee Integrity Risk in Agribusiness
When we consult for businesses that have unexplained symptoms of underperformance or suspect some employee integrity problems, we look at the following five risks: customer transactions, supplier transactions, cash and bank accounts, inventory, and payroll.
Customer Transaction Risk
This category includes all risks associated with client interactions. Examples from the introduction that fall into this category would be failing to register a sale, overcharging clients, accepting uncovered checks from “friends,” etc.
Supplier Transaction Risk
Specific risks associated with suppliers include overpayment, falsified records that show more products delivered than were actually the case, weigh bridge risk, accepting sub-par quality deliveries, taking inducements from suppliers for a supply contract, etc.
Cash and Bank Transaction Risk
This is the category where opportunity is often most common. It includes under-depositing of cash, unauthorized bank transfers, petty cash fraud.
Inventory Risk
Inventory is as good as cash. Any business has inventory, but any manufacturing or agri-processing business is particularly exposed to inventory risk. Stocks that disappear through retail theft or by the hand of employees are the biggest factor for concern. Another is the potential for break-ins by third-party actors seeking to remove inventory.
Payroll Risk
Ghost workers, unauthorized overtime, fraudulently changing bank account numbers, clocking in absent colleagues, etc. Payroll is generally an important part of the costs of a manufacturing business and so payroll risk is an important area to consider when assessing risk.
Preventive Strategies for Managing Integrity in African Agribusiness
The first step in managing employee integrity risk is recognizing theft as a failure of the organization. As they say, “opportunity makes the thief”. The solution lies in the conscious, continued elimination of opportunity. Sure, you might be a “victim” every now and then, but if employee integrity is a pervasive problem, it is in your power to change it and bring it down to manageable proportions. Victims do not have the power to change a situation. If instead, you consider that your processes failed, you’re in charge of building a solution. The situation is yours to improve.
I’m not saying that through solid business processes you will not get stolen from. You will, but it will be less than your competitors and you’ll be on a steady path to gain an additional competitive edge. Through your business processes, you can reduce the opportunity for theft and increase the probability of someone getting caught. The focus should be both on prevention and on dissuasion.
Generally, three types of action can be used to improve employee integrity challenges: employee support systems, surveillance and security, and transparent business processes. Our response to employee integrity challenges can combine several elements of the three, and we provide further details below.

1. Building Employee Support Systems
Right after the introduction to the topic of employee integrity for African agribusiness, we discussed the role of high poverty environments and how this plays an important role in integrity issues. One of the approaches towards employees in reducing employee integrity problems is providing them with a better safety net as financial emergencies are often a driving force behind integrity problems. These could be salary/allowance payments more frequently than once a month or insurance to cover life’s eventualities. We’ve also used techniques such as making payday predictable to spouses so that there is more control within the family before the money is spent over the weekend, leaving the family hungry two weeks later. This topic merits its own article, and so we’ll write on this separately in a future blog.
2. Implementing Effective Surveillance and Security Measures
Access control, camera systems, body check, bag check, and vehicle check (consult your local laws to find out who can do what and how under which conditions). These measures can be highly effective, and we’ve used them for rapid success when there was a suspicion of employee theft. Sometimes, by simply introducing a bag and body search, amazing results can be realized.
Camera systems can have a dissuasive effect. Please consult a professional when you do intend to put up a camera system. It has to be properly designed to avoid common mistakes. At a minimum, consider the following: put every camera in sight of another camera so that in case of tampering the person can be identified; make sure the cameras also see at night: use lighting or special infrared cameras; use general overview recordings to detect a suspect situation and close-up zooms at passages to do the identification (nothing as useless as a camera system that detects an incident but doesn’t allow you to identify the culprit). Also, schedule time for checking the recordings and doing regular maintenance. Avoid consumer-grade cameras as they generally can’t deal with the African heat, dust, and moisture levels. Consider how you will keep the camera system running in case there is a power outage, and the generator “fails” to start. The systems that we put in place could run autonomously on batteries for eight hours.
Through access control, you can limit the number of people that can find an “opportunity”. Restrict access to facilities, storage rooms, cold rooms, areas where cash is handled, etc. Map where high-value, high-opportunity goods are stored and control the exits. Infrastructure design can play a large role. Restricting the number of windows that can open and positioning them at levels that are difficult to access also plays a role in reducing opportunities.
3. Developing Transparent Business Processes
Accountability, responsibility, and feedback loops can curb fraud and theft. Let’s have a look at this through an example.
Example: How it Usually Goes
So, it’s decided! As MD you’re sending out your senior staff to do stock counts at the end of the month and take on the most important one yourself. Everyone goes about their business and returns with a stack of A4 paper full of hand-scribbled notes of the inventory that was counted. The papers are missing signatures from the person responsible for the stock and the person checking them. They are handed over to the accounts clerk in charge of inventory to reconcile.
Because most of the handwriting is hard to read and different people have named the same item differently, the clerk is running from person to person to find out what inventory item was exactly meant by the scribbled note “premium widget B”. As it turns out, your senior management wasn’t sufficiently familiar with all the items, especially the person who was hired three months ago and made a terrible mess of inventory identification.
The clerk does as well a job as possible and manages to send out reconciliations to the people responsible for the stock a week before month-end, despite not having been able to resolve most issues. About a week later, the clerk gets them back with angry notes from the people responsible for the stock about the numerous errors in the data and the time they’ve been wasting to answer his questions. As the end of the month is now near and the clerk is overwhelmed, nothing gets done, we’re rushing into the next stock count, and no one is held accountable.
This scenario is a recipe for disaster: you’ve just sent out your senior team to count inventory in an effort to improve the transparency of your business processes and reduce the problem of integrity challenges. But what happens is the opposite: the people responsible for your inventory are not held accountable and it becomes quite obvious that the business is incapable of tracking and reconciling stock accurately. In effect, you’ve both reduced dissuasion and increased opportunity by clarifying that it is possible to get away with anything.
Example: How it Should be Done
An ideal inventory count would look something like this: prior to the count, the clerk in charge of inventory prints out the list of items that should be present in the warehouse concerned. The inventory items are grouped by category. The new person takes this list to the warehouse and finds the inventory organized by category too. Pallets, shelves, containers, freezers, cupboards (whatever your situation) are labeled according to the categories of items to be found here. Individual items or their storage bins are clearly labeled with the product code and description.
The printed list serves as a guide for the person conducting the stock take and the only thing that the person has to do is to write down the quantities. The list is crystal clear about the units to be used in the inventory check too: kilograms, the number of trays of 100 individual items, etc. (I’ve had someone actually count the screws that were in a storage bin instead of weighing them: never assume that the units are obvious!).
The person executing the stock count takes the list (signed by the person responsible and himself/herself) back to the accounts department where the figures are entered into your stock control software immediately. A variance report comes out which is checked for errors and obvious mistakes. These are resolved and corrected over the next one or two working days before being sent to the person responsible for the inventory. That person is given five working days to respond to any discrepancies and explain any differences.
Within 10 working days, you have completed your whole inventory control process and now know for sure if you have problems or not. Any problems that have become apparent are escalated to senior management for resolution.
Implementing a Comprehensive Risk Management Framework
The following is a four-step risk management framework that we apply in our work.
The Four Steps of Effective Risk Management
Identifying risks in operations
This step involves the listing of potential risks. A useful method is brainstorming. After brainstorming, it is important to spend some time to truly understand the risks.
Assessing the impact and probability of risks
Once you have a list of risks and they are well understood, it is important to assess them based on their impact and their probability of occurring.
Formulating responses to business risks
Based on the mapping of the risks in the previous step, a risk response can be formulated for the risks that are most material to the organization. In general, we try to avoid risks where possible, and to reduce the impact in case something goes wrong. A third option is to transfer the risk to a third party and the final option is to accept a risk when its impact is manageable or when the costs of controlling it outweigh the benefits.
Monitoring and Controlling Risk Responses
This is the process of executing the plans and monitoring and adjusting them as needed.
Risk Assessment Techniques to Guide Business Decisions
The assessment of risk is best done through the use of a matrix. See figure 1. On the vertical axis, we have the probability of a risk occurring and on the horizontal axis its impact. We’d like to reduce both factors together and push them as much as possible towards the low probability – low impact quadrant. Our focus is obviously on the high probability and high impact risks, while also taking a hard look at the “fat tail” risks of low probability events but with potentially catastrophic impact. In the figure, we have plotted three examples which we will discuss later in this article.
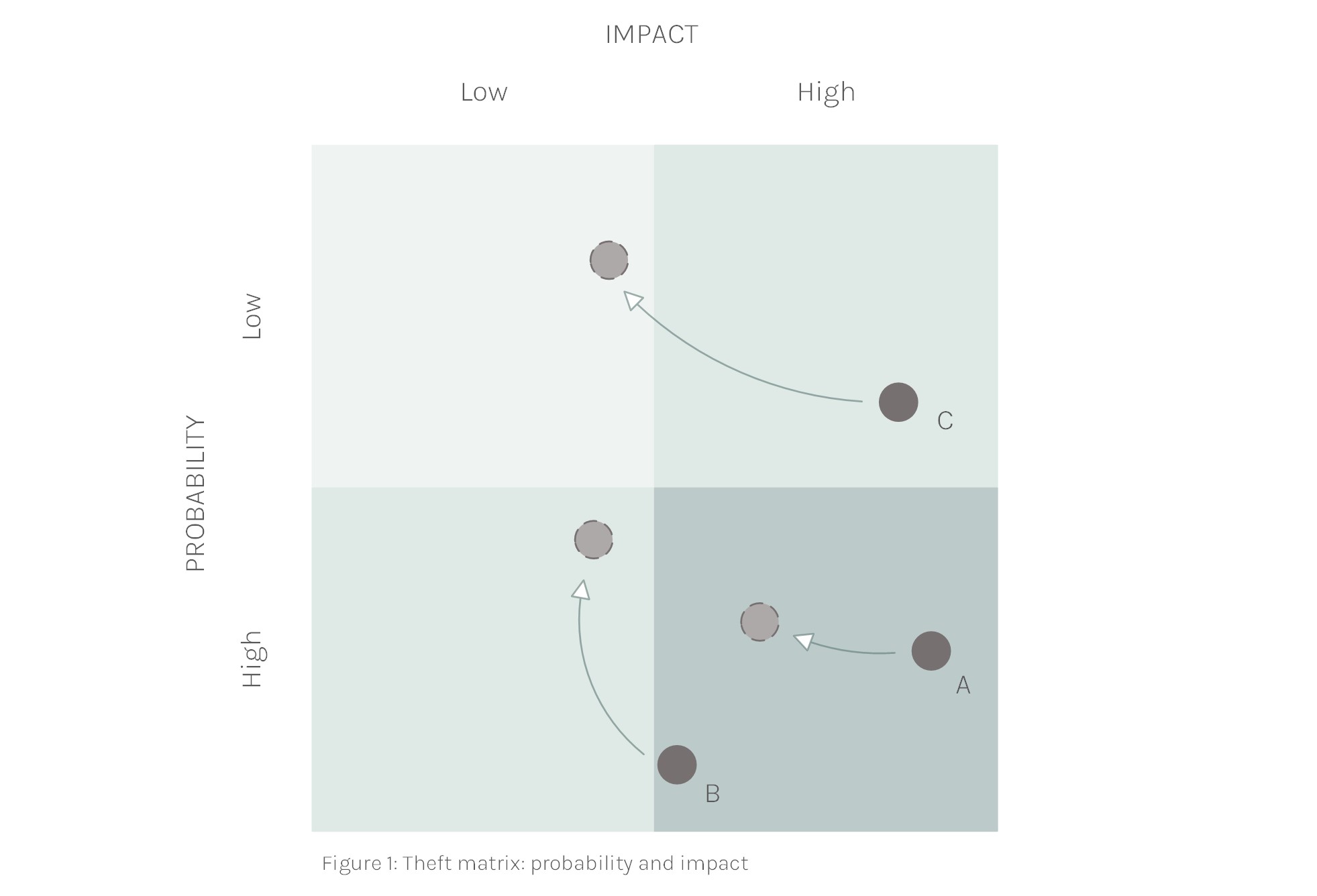
Case Studies in Risk Reduction
Case Study A: Significant Daily Cash Collections at Multiple Sites
In this example, cash collections could be the result of daily retail sales through a network of selling points. We’d flag these as medium-high probability, and high impact. Collections are typically important, and the remoteness of sites contributes to an increase in risk as they are harder to control. Depending on the number of locations, there’d be more or less risk to the business. The key concern here is to make sure that all the cash collected is being deposited into the bank. Sounds simple.
In practice, this is going to be a bit of a challenge. The first step is to know for certain what the daily cash sales are. Then a solid process needs to be in place to verify that this cash has gone into the bank. The higher the frequency of such a depositing process, the less money is at risk and so the lower the impact of any eventuality.
In the past, we’ve implemented a process whereby sales were registered electronically, communicated with the head office automatically overnight (not so obvious in areas with poor internet connections) and the following morning before 10 am the cash deposits bank account was reconciled, and a call would go out to the relevant salesperson if there were any discrepancies. The window of opportunity in this case is short, the maximum amount at risk is one day’s worth of cash sales, and the fact that receiving a call from the head office by the finance director if a deposit was late or incomplete is an important dissuasive factor.
In figure 1, we’ve plotted the result of such a business process improvement: a reduction in impact and some probability as the result of a business process improvement effort. The impact in this example could be cut further by increasing the frequency of cash deposits, for example, by making a cash deposit halfway through the day. This could potentially push the impact of this example towards “low”.
Case Study B: Inventory Theft in Agribusiness
For example B, we’ve taken a manufacturer who converts raw materials to finished goods and some sort of logistics operation to distribute the product. The plotting of example B in the matrix is arguably debatable. A single occurrence of theft of some company items is not going to be a high-impact event. However, the impact can become very large if this is repeated continuously, day by day: margins can be eroded to such levels that cash flow dries up and the company goes into distress. Unchecked “pilferage” can lead to the closure of your business.
To illustrate this example, we’ve plotted inventory theft as a high probability event with medium impact. Low volume, high-value goods are more at risk than high volume, low-value goods. Products that are easy to sell in local markets are also at higher risk: fuel and food items as well as tools and parts for common machinery (solar panels and pumps anyone?) would be of key concern.
How to go about the reduction of probability and impact on inventory? As a start, reducing inventory would reduce the value at risk and lean manufacturing offers some tools to achieve this. An easy approach is one where for each stock item maximum levels are set in accordance with the need to cover sales or provide desired levels of business resilience. Standardization of production lines, vehicles, and the use of spare parts can also bring down required stock levels. The simpler, the better.
Second, transparency and dissuasion need to be addressed. You’d need to make clear who is responsible for which item in which area. If more than one person is responsible, no one is. You’d need to keep accurate track of what goes in, what goes out, and what the theoretical stock levels are. Then, you’d need to verify regularly if the stock levels in practice are the same as the theory: stock counts. The frequency of the stock counts would depend on the risk analysis. If opportunity as well as the value at risk are high, then you’d need to do counts more regularly than if the opportunity and value were low. Regular planned and impromptu stock counts are the cornerstone of inventory theft prevention.
In certain problem cases, we’ve gone so far as to do weekly stock counts of entire warehouse areas. Yes, that is cumbersome but in problematic cases, this is what is required to turn a situation around. Immediate reconciliation and delivery of a variance report, holding the person responsible for the product accountable, has a wonderful effect on data accuracy and bringing variance down to manageable proportions. Once business processes are working and variances are manageable, the frequency of stock counts can be reduced to monthly counts for example.
Low inventory levels, together with accurate, transparent stock keeping and regular inventory checks will bring down the probability of some of your staff considering the resolution of a personal cash flow problem through “shrinkage” or considering “pilferage” as a secondary career or an employment perk. Opportunity makes the thief. Eliminate it wherever you can.
Case Study C: Transferring Risk Related to Large Volumes of Commodities
For example C, we’ve taken a case where a business is engaged in the purchase of large volumes of agricultural commodities. Large and bulky volumes are hard to steal so the probability is low, but when it happens, its impact can be very high. I’ve heard more than one story from other business leaders who had a complete warehouse emptied overnight. Security staff is in on the deal, bags of the commodity are deposited on the inside of the wall fence and used as a platform to load trucks on the other side. A small fleet of trucks and laborers is organized to empty the warehouse in a matter of a few hours during the night. The merchandise being a commodity, it is almost untraceable and quickly sold on local markets.
Outsourcing the responsibility over the warehouse is one way of reducing impact: specialized companies exist that can handle this for you. It’s expensive but for me, it was a way to sleep easy at night knowing that if anything were to happen, the value of our inventory was assured. Obviously, you’d still be exposed to some risks due to foregone sales and opportunity costs in case of such an event, but overall, this is much more manageable than facing the financial loss as well.
Reducing probability of theft of large volumes of product comes from factors such as proper site selection, access control (layered perimeters), (armed) security guards and making sure that no single person is capable of opening up the warehouse (double locks). I used to make it a habit to not only rely on the armed guards of the security company working for the stock manager, but I’d also post my own guards. It adds another level of collusion necessary to gain access to our valuable inventory.
In the probability – impact matrix, the combined implementation of these business processes would result in a substantial decrease in impact and a non-negligible improvement in probability too.
Case Studies Summary
I’m pretty sure that there are many other examples that you can come up with and an important one that I’ve left out is large cash payments to suppliers. We all know that digital payments would be much less risky but because electronic payments are still slow most of the time and the farmer members of cooperatives impatient to receive their money (and situated in remote locations, far from banks) most of us still practice the occasional cash payment. Rapid payments to farmers in heated commodity markets are a source of competitive advantage and a well-managed payment system contributes to this. To reduce your risk, use the same matrix approach as the three examples: plot the factors out according to probability and impact and brainstorm ideas to reduce the most material ones.
Leadership’s Role in Risk Management
Senior management needs to lead the effort to manage risk. If this is delegated, it signals that in fact, controlling these risks is not that important. Senior management needs to set time aside to be a part of risk management processes on a regular basis and it should be a standard topic on the agenda of the board. Bank reconciliations should not be left to junior accountants and stock counts should be co-executed by senior managers wherever there is an identified high risk.
The benefits go beyond dissuasion. Well-run business processes lead to transparency. Inventory has a lot to tell about your business. When you are involved with stock counts yourselves, you’ll find out which products move fast or slow, if there are any legacy items that have become obsolete and if there are any storage challenges that lead to deterioration of inventory. You’ll get to spend valuable time with frontline staff, find out more about their perspective on the business, and gain ideas for what can be improved. You’ll also get a better idea of the customer’s view on your business. These are all welcome side effects of getting senior management involved in regular stock counts.
If you have a lot of sites to control, it would be unrealistic to get them all done by your senior management. It is perfectly fine to get junior staff from accounting involved, for example. Just make sure it’s never the same person who executes an inventory count at the same place twice in a row and shake things up every now and then with an unannounced inventory count by someone from your senior staff.
Leveraging technology for business integrity
Transparent business processes can only be realized through the use of technology. Technology will enable three crucial aspects of inventory control:
- Codification and labeling of inventory: the entire organization uses the same language to describe and communicate about an item. This enables everyone, including your new recruits, to know what we’re talking about.
- One version of the truth through data accuracy and integrity: The use of software that has a frontend for the user interface and a backend such as SQL for your database (on site or in the cloud) will make it easier for your staff to quickly and accurately fill in forms such as dispatch and delivery notes while at the same time ensuring your data integrity. Once something is in the database, it cannot be deleted or altered in any way.
- Access: Because software can work with user profiles, only authorized people can have access to the forms and advanced features that allow you to control the flow of your goods and cash. The advantage is also that multiple people can work on your data at the same time.
The above can be done with enterprise resource planning software (ERP) from companies such as Microsoft, Sage, or Odoo. They have solutions for different business types and off-the-shelf packages that are quite complete and will help you get a grip on your organization. In most cases, there is no need for expensive customizations. Things like bank and stock reconciliations can be automated by these packages too: most of the time you can simply import your bank or inventory data and reconciliations will be made automatically, matching amounts for example.
Now, incredible things can be done with Excel and for analysis work it is still unbeaten. If you need a solution fast and you have just one senior person working on it, this is the way to go. In problem situations where I need to analyze a situation in a business where tracking of inventory or cash is problematic, Excel is what I use. Also, before moving to more advanced software, modeling in Excel will allow you to mature your processes before putting them in much harder-to-change ERP software. This will save you money and time in the long run.
The Most Common Pitfall in Managing Business Processes
There’s nothing revolutionary in what I’ve written about getting your processes controlled. It is also not overly complicated. And yet, a scenario of unchecked employee integrity problems is a major cause of African agribusiness companies struggling with cash flow, profitability, and survival. What started as an easy-to-control business with a few employees and an Excel sheet to keep processes transparent can grow into operations over several sites with many employees. Management is busy with managing growth, realizing projects, and driving turnover. Taking care of stock counts, delivery notes, and data integrity is not as exciting.
Most learn the hard way that the foundations for growth were not in place and have to go back to the drawing board if they get that chance. A quote attributed to Bill Hewlett, co-founder of Hewlett Packard, says that more companies die of indigestion than starvation. A very apt description for most companies that do not take the time to do the less exciting groundwork to create the conditions required for successful business growth.
Conclusion
Employee support systems, surveillance and security, and effective, transparent business processes will bring down staff integrity problems to manageable proportions. Preconditions for success are to make this your senior managers’ jobs. This stuff is not as exciting as the growth projects you are working on, but transparent business processes are a cornerstone and a precondition for successful growth of your African agribusiness SME. Use technology to eliminate noise and keep the time investment of your senior staff acceptable so that there is plenty of time left for the more exciting projects.
Getting accurate data, as close to real-time as possible, and well-analyzed will not only resolve integrity problems but also hand you the information to improve business performance. Short feedback cycles based on accurate data are critical to rapid learning and innovation. So, your whole system of business processes focused on controls over cash and inventory also provides the basis for your innovation and problem-solving processes.





